Pricing
In the news | Cloaked founders were recently featured on CBS
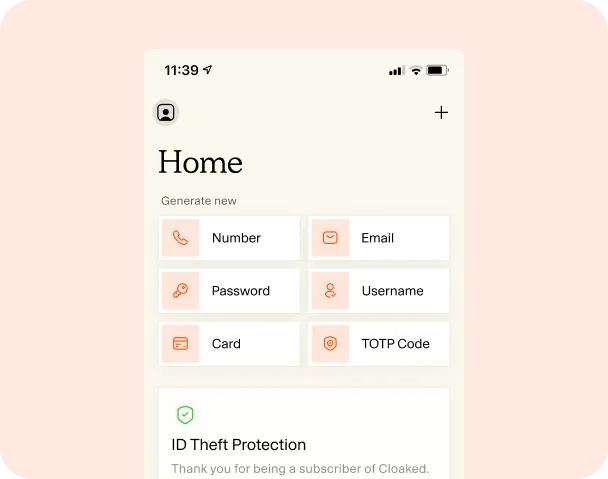
Identity Theft Protection
$1 million insurance against identity theft
Data Removal
Remove personal info from 120+ data brokers
AI Defense
Fight back against AI deepfakes and scams
Family Sharing
Secure and protect your family’s data
Call Guard
Block spam calls and robocalls instantly
Cloaked Pay
A secure and private way to pay
VPN and Browser Protection • New
Browse the internet privately and safely
Dark Web & SSN Monitoring
Real-time alerts for dark web exposures
Just released
Product
Phone Number and Email Aliases
Never give out your personal info again
Coming soon
Autocloak AI
Alias management powered by AI
Cloaked founders were recently featured on CBS